If you are an avid iMessage user, you’d definitely use emojis to add a touch of color and emotion to your messages. But what if you want to express yourself by combining two or more emojis on an iPhone? Yes, this is possible. On your iPhone, you can stack multiple emojis on top of each other and take your texting game to the next level. In this article, I’ll show you how to combine emojis on an iPhone.
How to stack emoji on your iPhone
To combine emojis on your iPhone, you first need to send an emoji as a sticker and then stack it up with other emojis from your iOS keyboard.
Step 1: Send an emoji as a sticker in iMessage
If you use WhatsApp, you might know how the small heart emoji transforms into a larger animated sticker whenever you send it without text. The same can be done in iMessage for various emojis, but there’s a twist.
In a regular iMessage, an emoji sent without text will display in the chat box without a bubble. However, its size remains normal. The trick to send it as a giant animated sticker is to drag the emoji from the keyboard and drop it in the text input field.
- Open the Messages app and head to a conversation.
- Tap the text box at the bottom to access the keyboard.
- Now, tap the emoji icon at the bottom left corner of the keyboard.
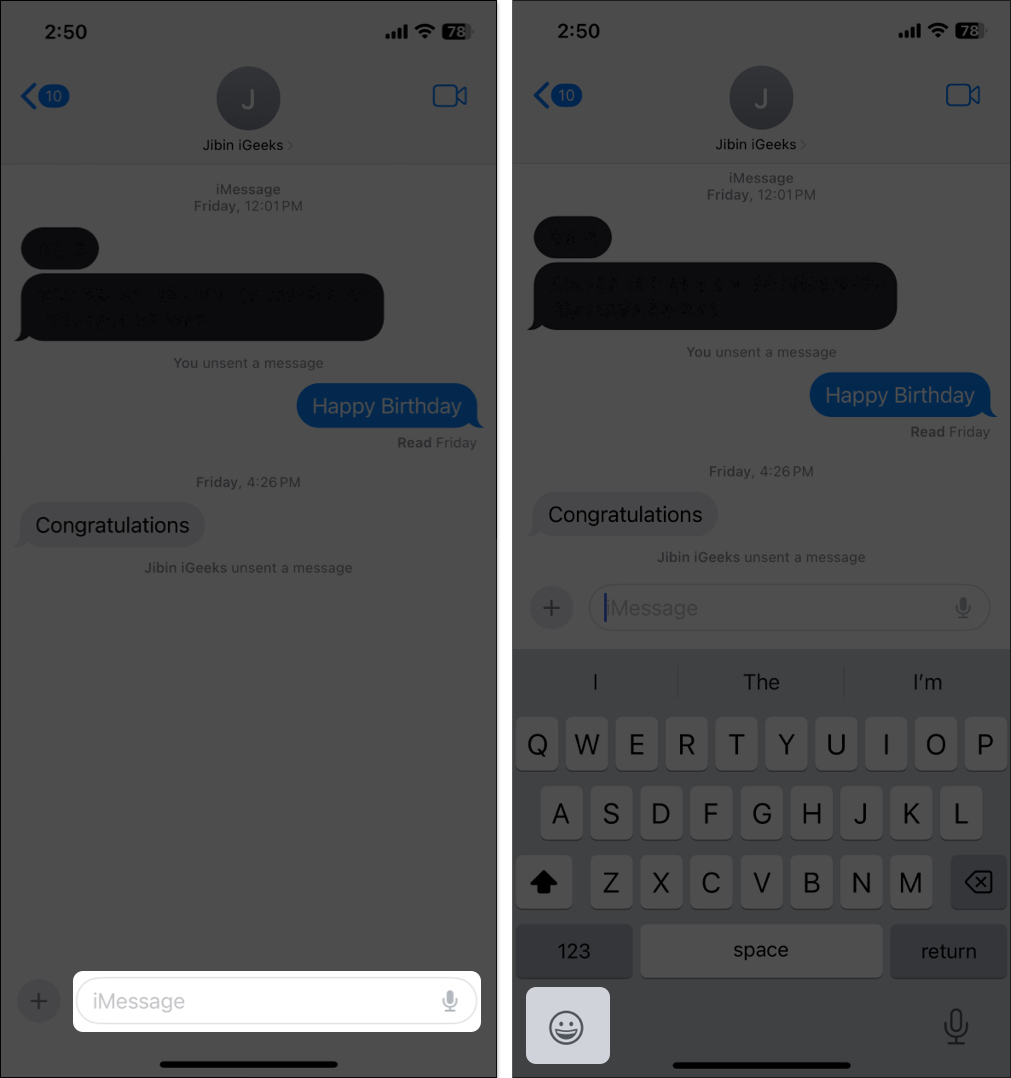
- Tap and hold the emoji you want to send.
- Alternatively, you can use different emoji skin tones for certain emojis.
- If the emoji you selected has multiple skin tone options, lift your finger and tap & hold the skin tone option you want to use.
- Now, drag the selected emoji to the iMessage text field and leave it once the green “+” (plus) icon appears.
- In a few seconds, the emoji will transform into a giant sticker. Hit the blue send icon (upward arrow) to share the sticker.
Step 2: Add layers of emojis
Now that you have sent an emoji as a sticker in a message on your iPhone, you can drag and drop N number of emojis over it to create your very own emoji stack.
Here, the process is simpler. You can drag the emoji from the keyboard and drop it directly on the sticker that you just sent. There’s no need to use the text field!
- Send your first giant emoji using the method mentioned above.
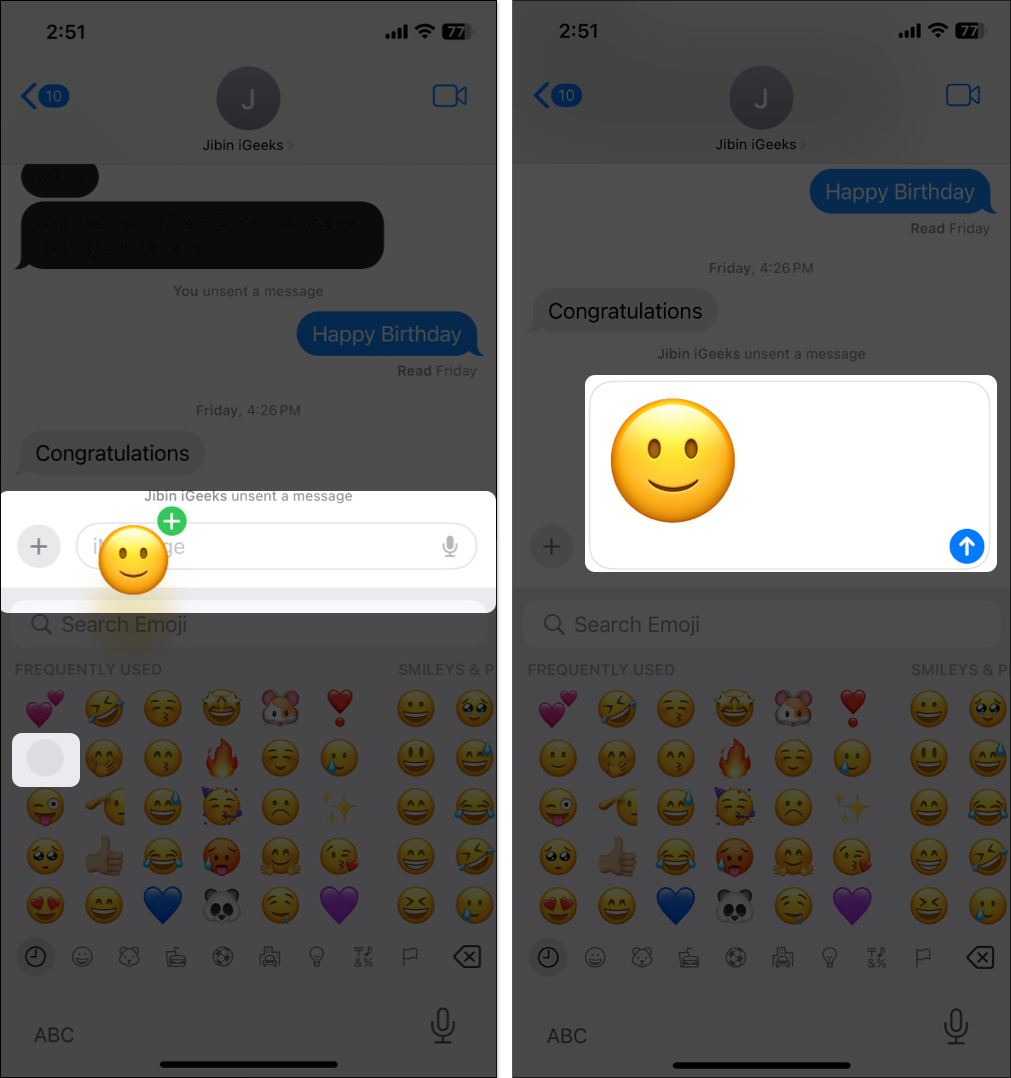
- Again, open the keyboard and tap the emoji icon at the bottom left.
- Pick the emoji you want to layer on top of it. Drag and drop it on the first emoji you sent.
- Once you are satisfied with the placement, release your finger, and the emoji will be added to the top or alongside the first emoji sticker.
You can repeat this process to add as many emojis as you want to your emoji stack.
Adding a new emoji to the sent emoji stack will automatically reflect on the recipient’s screen as the original message.
Pro Tip
You can also change the size and orientation of the emojis. For example, you can use two fingers to stretch and convert the emoji into a giant or tiny one before sending it.
How to edit or delete emoji stacks on iPhone
Once you have created and sent an emoji stack in iMessage, there may come an instance where you think you overdid the emojis or accidentally added the wrong emoji.
In that case, you can easily remove the emojis from the stack or delete the emoji stack altogether.
Edit or reposition an emoji
- To edit an emoji’s size, orientation, and position in the sent emoji stack, tap and hold the emoji.
- The emoji will see a ripple effect kind of animation and bulk up in size, indicating that you are in control of it now.
- Drag the emoji to reposition it, or use your other finger to change its size or orientation.
- Once done, release your finger, and the emoji will reflect the changes.
Delete emojis from the stack
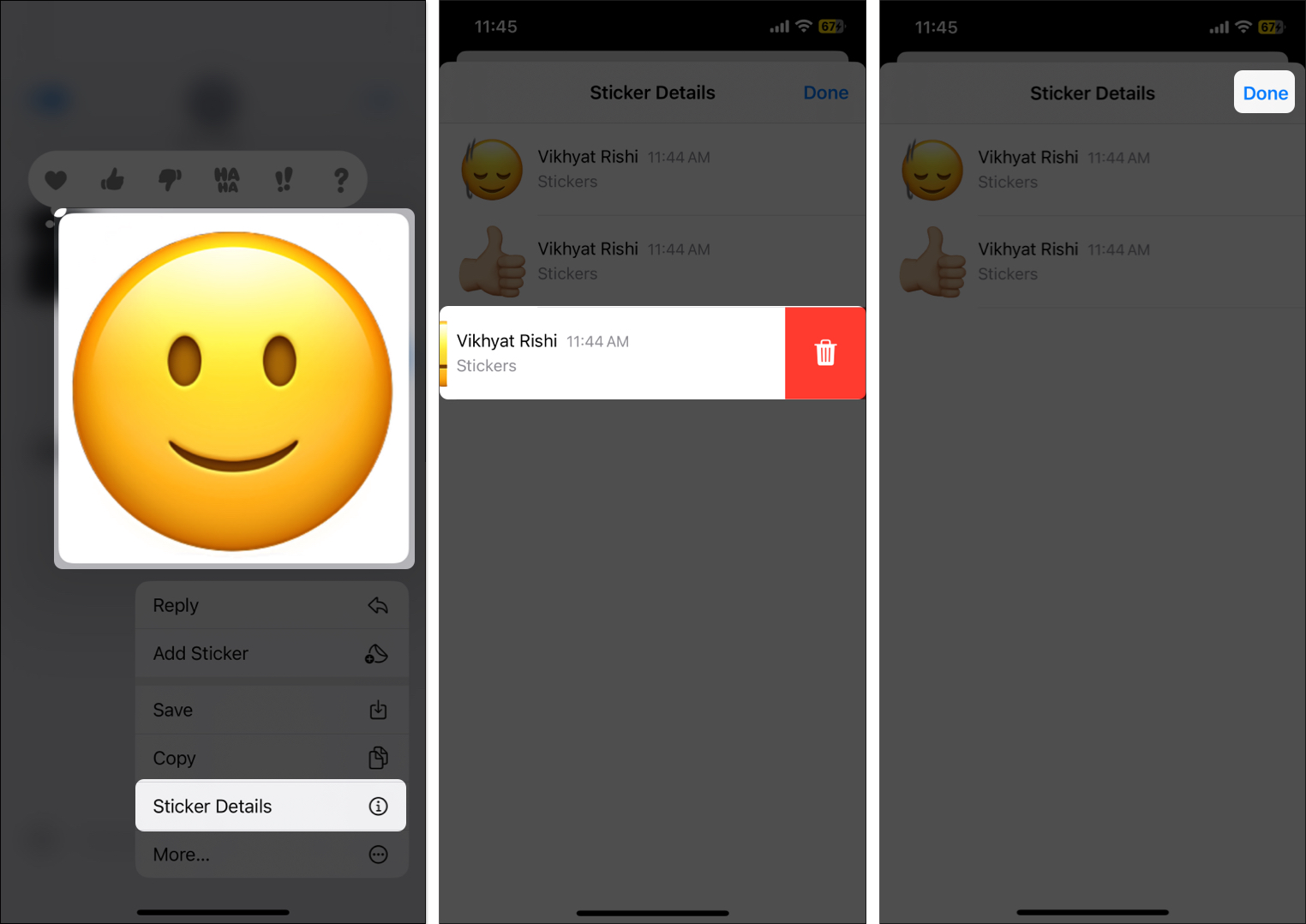
- Tap and hold the first emoji in the sent emoji stack.
- Choose the Sticker details option in the pop-up that appears.
- Swipe left on the emoji you want to delete and tap the Delete (trash) button.
- Repeat the process for all the emojis you want to remove from the stack.
- Once satisfied, tap Done at the top right corner.
- Alternatively, you can delete the entire emoji stack, similar to how you delete an iMessage on your iPhone.
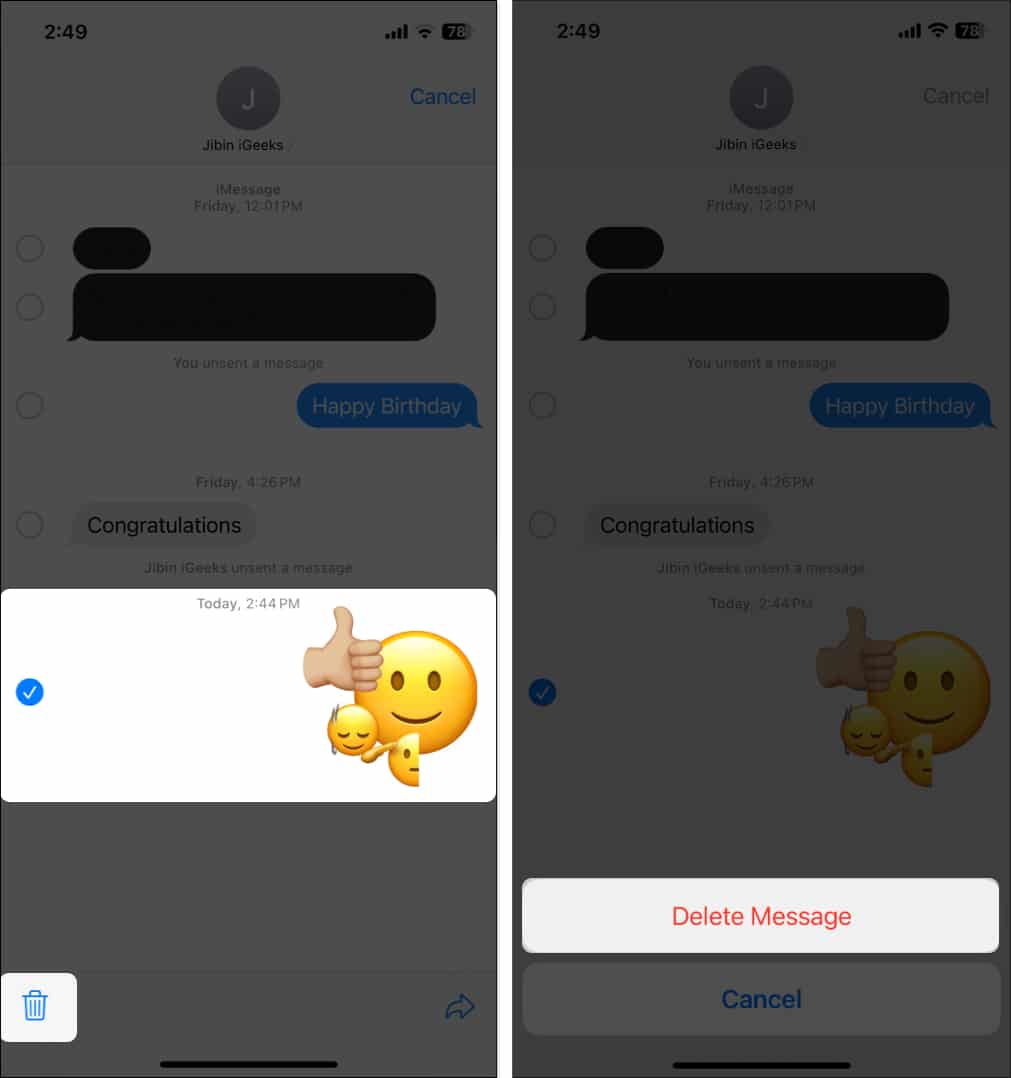
This method only works on a combination of emojis. If you have sent an individual animated sticker, you can Undo Send within two minutes of sending it.
Can’t combine emojis on iPhone? How to fix it
While combining emojis on the iPhone is as straightforward as possible, a few users may encounter issues or limitations. To start off, the Messages app can only create and send an emoji stack via iMessage; the same is not possible via SMS.
If you’re using iMessage and still having trouble with combining emojis, here are some troubleshooting tips for you.
- Restart your iPhone: Restarting your iPhone is the first thing you must do whenever you encounter an issue. Most of the time, restarting can fix minor software glitches your iPhone might be experiencing. Restart your iPhone and try combining the emojis again.
- Reset Keyboard Settings: This will reset any custom keyboard settings you made previously and might fix the emoji-combining issue. Open Settings → General → Transfer or Reset iPhone → Tap Reset → Choose Reset Keyboard Dictionary → Enter your passcode and confirm your choice.
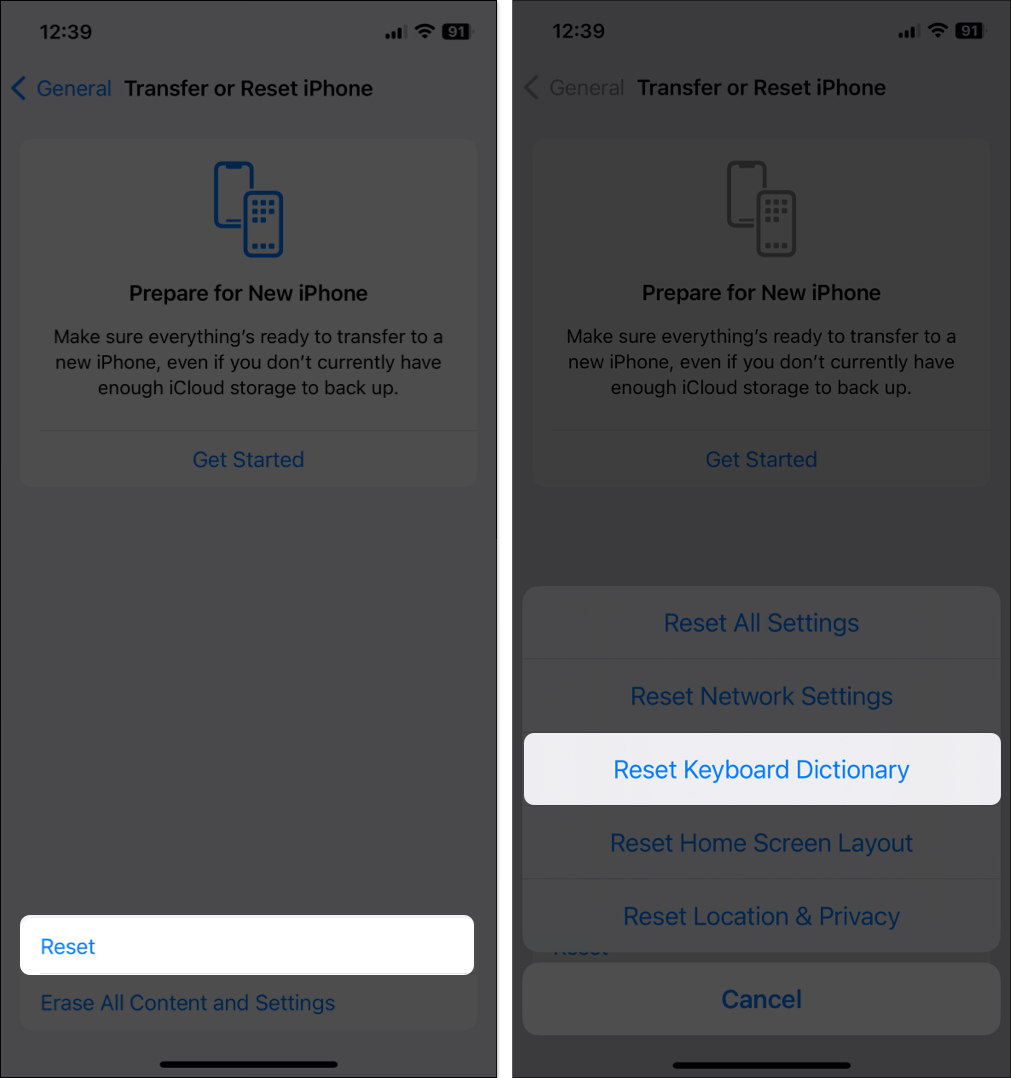
- Update iOS: iOS updates often include bug fixes and improvements that can address different issues, such as combined emojis not working on your iPhone. Just go to Settings → General → Software Update → Tap Update Now if you see one available.
- Use a third-party app to combine emojis: If the issue persists, try using the best iPhone emoji apps available on the App Store, such as Emoji Me Face Maker or Bitmoji, to create personalized and unique emoji stickers.
Signing off…
And that’s it; this is how you can combine and create an emoji stack on your iPhone. With just a few simple steps, you can elevate your messaging experience, making it more fun.
Did you enjoy learning about this iMessage hack? If yes, then I’d recommend our detailed guide for more such iMessage tips and tricks!
🗣️ Our site is supported by our readers like you. When you purchase through our links, we earn a small commission. Read Disclaimer.

